Many of you might have seen that a new feature is present in your Azure AD portal:
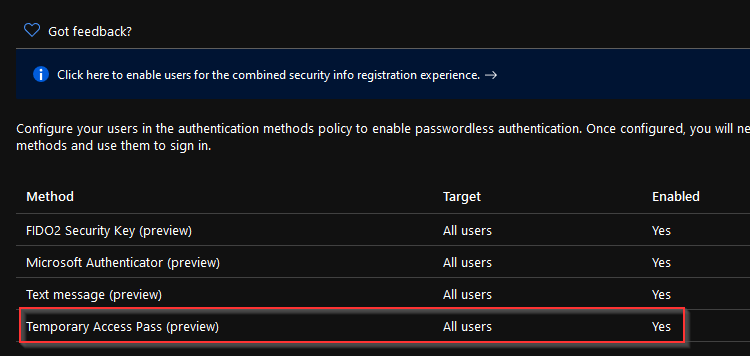
What is this feature? Well as far as I know, this is planned to be used for onboarding and recovery primarily.
Onboarding to Azure AD for new employees, allowing users to sign in using strong credentials for the first time and configure their FIDO2 key, Authenticator app or what have you.
Recovery in the sense that you might have lost your MFA device (no, email is not a valid MFA option in my opinion) and you need to re-configure your Authenticator app / FIDO2 key.
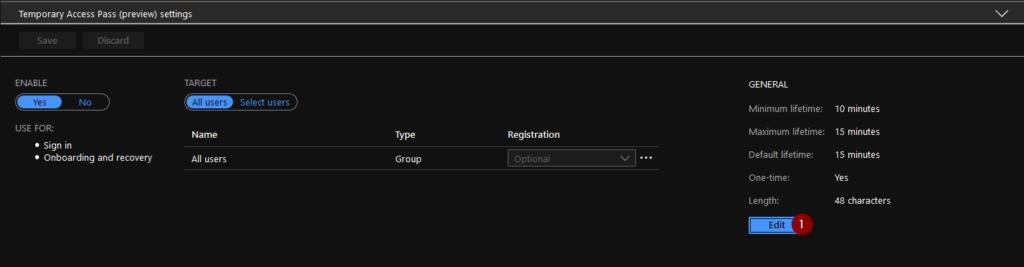
The settings are quite straight forward, you can configure the lifetime of the Temporary Access Pass (TAP) by enabling the feature and clicking “Edit”.
These settings are possible to configure:
Target (which users are meant to be able to use TAP)
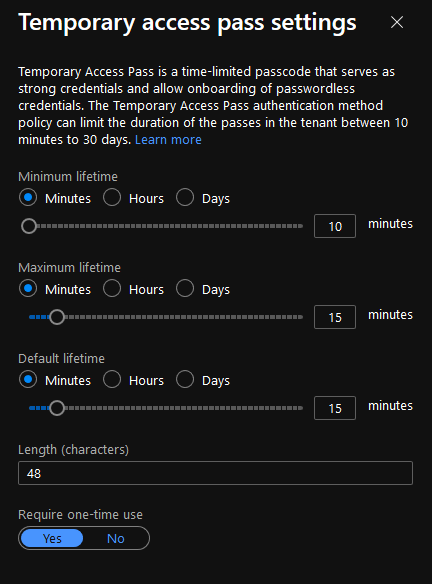
- Minimum Lifetime (10 minutes – 30 days)
- Maximum Lifetime (10 minutes – 30 days)
- Default Lifetime (10 minutes – 30 days)
- One-time (Yes/No)
- Length (8-48 characters)
Okay, how do we use this feature, or atleast try it out? Well since it´s quite new in the portal, the documentation is non-existent as of now. But, since everything in Azure AD is configurable via Graph, let´s try to use the explorer to configure this setting for a user.
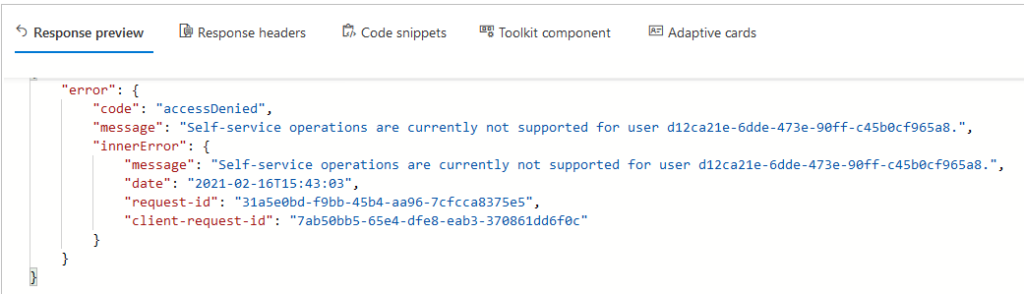
NOTE: You are not allowed to set this feature for your own user:
First things first, you need to have your Graph API permissions in order. To use this feature you need to have permission to the following:
UserAuthenticationMethod.ReadWrite.All
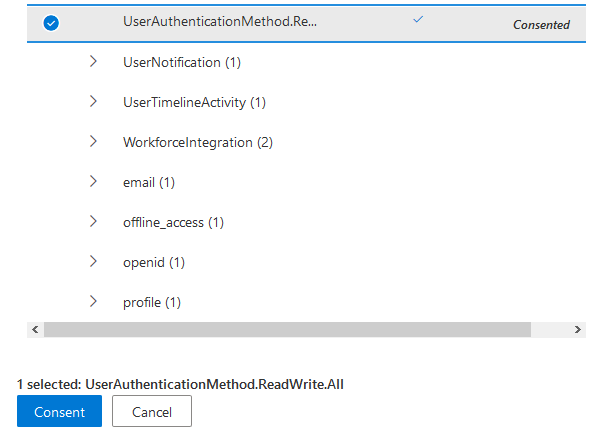
Once permissions are in place, the procedure for activating a TAP for a user is quite easy.
You issue a POST statement to the API using the following statement:
POST https://graph.microsoft.com/beta/users/<ObjectId of the user>/authentication/temporaryAccessPassMethods
With an empty JSON payload
{}
If you get a 201 response, the response will allow you to see the TAP for the user:
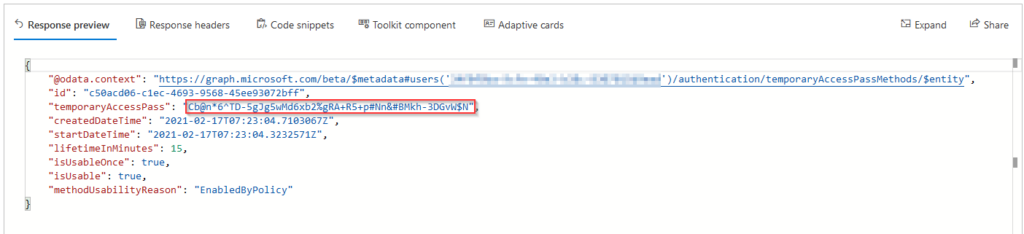
All right, now we have created a TAP for a user in our Azure AD. Let´s try to use it for sign-on.
Here, I have navigated to https://myapps.microsoft.com and entered the users email.
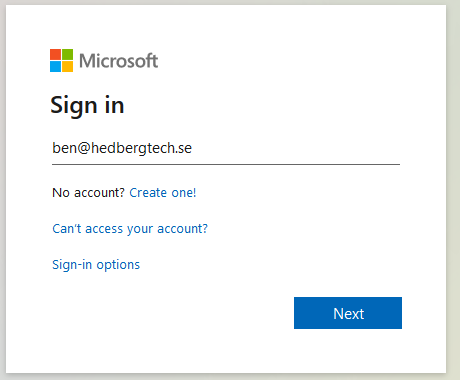
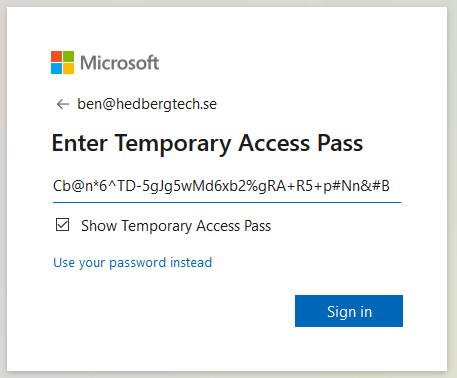
Clicking on “Next” takes me to a new sign-in prompt which asks me to enter the TAP:
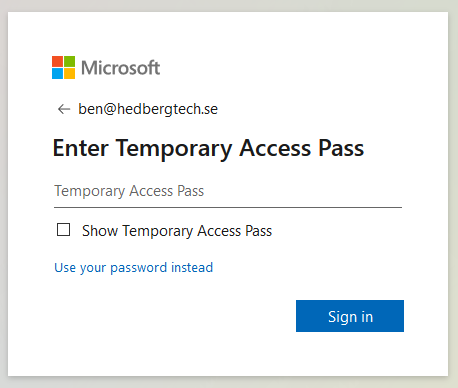
I enter the 48 character long TAP, click Sign In, and presto! We are in!

This feature will in no doubt in my mind ease the transition to Passwordless, not being asked to provide your password even once. This will also be a useable feature when it comes to break-glass scenarios, recovery of MFA etc..
There you have it, how to use the feature Temporary Access Pass. Go try it out on your tenant!